- Name - SRM
- Category - Reverse Engineering
- Points - 50
- Description - The flag is : The valid serial number
- Binary - Download here
Yep it's a Windows binary! It's not everyday we encounter a Windows binary in a CTF. Run it:
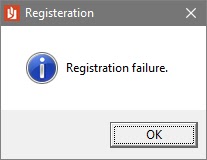
Looks like a keygen. Inputting garbage in both fields pops up the following message box:
In IDA we notice that the validation logic resides in the DialogFunc() function. The first check is done on the email address.
The functions accept any valid email address so test@test.com will do (for now ?). The error message now is different:
Next is the Serial Number validation. The code is quite simple:
if ( strlen(v11) != 16
|| v11[0] != 67
|| v23 != 88
|| v11[1] != 90
|| v11[1] + v22 != 155
|| v11[2] != 57
|| v11[2] + v21 != 155
|| v11[3] != 100
|| v20 != 55
|| v12 != 109
|| v19 != 71
|| v13 != 113
|| v13 + v18 != 170
|| v14 != 52
|| v17 != 103
|| v15 != 99
|| v16 != 56 )
{
sub_4030C7(&Text, 256, &v28);
}
else
{
sub_4030C7(&Text, 256, &v25);
sub_403121(&Text, 256, v11);
}
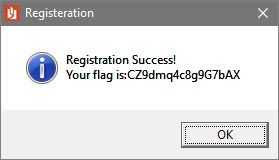
The serial number has to be 16 characters long (line 1). The checks are not sequential but they do follow a pattern: 1st, last, 2nd, 2nd to last, 3rd, 3rd to last, etc. At this point either go through it step by step or order the variables: v11[0], v11[1], v11[2], v11[3], v12, v13, .., v23. Converting from decimal to ASCII we get CZ9dmq4c8g9G7bAX. Input the email and serial number:



No comments:
Post a Comment